Information technology professionals often aim to earn certifications that boost their careers and expand their skillsets. Among ISACA's globally recognized credentials, the Certified Information Systems Auditor (CISA) and Certified Information Security Manager (CISM) certifications are highly regarded. Understanding the distinct roles they prepare you for can be the first step in your career success.

This blog explores the day-to-day responsibilities of CISA and CISM professionals, showcasing how these certifications shape roles within the IT and cybersecurity fields. Whether you're considering one of these certifications or simply curious about these career paths, this comparison will help clarify their unique contributions to the industry.
Understanding ISACA and its Certification Programs
ISACA, the global leader in IT governance, risk, and cybersecurity certifications, has been at the forefront of equipping IT professionals with the tools to excel. First established in 1969, ISACA now boasts 460,000 professionals engaging in its pool of certifications, research, and training programs.
Among ISACA's flagship certifications, CISA emphasizes IT auditing, control, and assurance, while CISM targets leadership in cybersecurity management. Both certifications enjoy global recognition and are frequently cited in job descriptions for high-paying and high-demand roles. Now, let's explore what professionals holding these certifications actually do.
CISA vs. CISM: A Side-by-Side Comparison
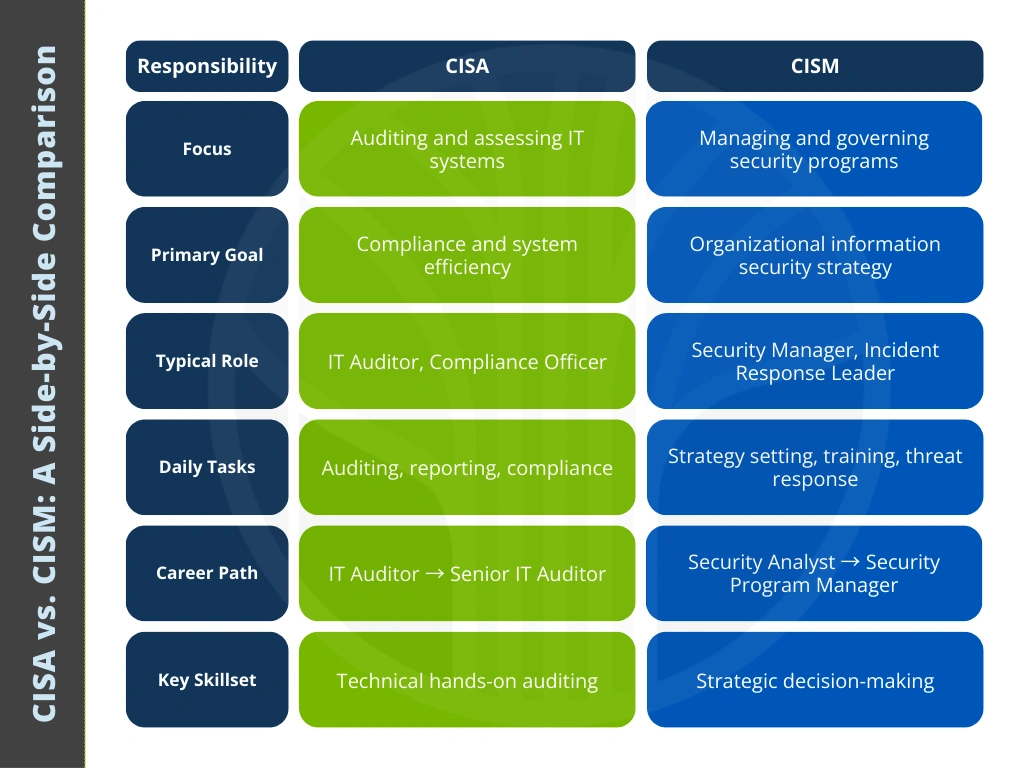
Both certifications complement each other, especially in large enterprises where auditing and management teams work closely.
The Role of a CISA Professional: Responsibilities and Daily Activities
A Certified Information Systems Auditor (CISA) specializes in ensuring that an organization's IT systems meet compliance and performance standards. These professionals wear many hats, ranging from auditor to IT governance advisor. Here’s a glimpse into a typical day:
Morning Tasks
- Audit Planning
A CISA-certified IT auditor typically starts their day by reviewing audit schedules and planning their next assessment. They analyze business systems, evaluate risk management strategies, and draft the frameworks they'll use for system evaluations.
- Documentation Review
They often spend time poring over system controls, access logs, and compliance documents to ensure that policies align with legal requirements and industry standards.
Midday Activities
- Performing System Audits
CISA professionals are hands-on with systems, testing for vulnerabilities, efficiency gaps, and control weaknesses. For instance, they may use automated tools to analyze user permissions, system redundancies, or server configurations.
- Presenting Findings
After completing audits, they document their observations for managers or stakeholders. Reports may include risk ratings, compliance suggestions, and correction plans.
Afternoon Responsibilities
- Collaborating with Teams
Effective auditors don’t work in isolation. CISAs engage with IT teams to review audit results and propose actionable improvements. They’ll also advise leadership on aligning IT objectives with broader business goals.
Sound structured? Yes! The role’s foundation lies in precision and thoroughness.
Key Competencies for CISA Professionals:
- Detecting vulnerabilities in IT systems
- Performing risk-based audits
- Compliance with regulatory frameworks
CISA professionals ensure organizations run secure, efficient, and legally compliant IT environments.
The Role of a CISM Professional: Responsibilities and Daily Activities
On the other side of the spectrum, a Certified Information Security Manager (CISM) is a leader responsible for shaping an organization's cybersecurity strategy. While the CISA role is heavily technical, CISM professionals focus on the policy, strategy, and leadership aspects of information security.
Morning Tasks
- Setting Security Strategy
CISMs often kick off their day by reviewing security roadmaps and aligning information security strategies with broader enterprise goals.
- Monitoring Threat Landscapes
They consult ongoing threat intelligence reports to understand potential external and internal cybersecurity threats. Emerging vulnerabilities may prompt strategic shifts to strengthen defenses.
Midday Activities
- Incident Response Coordination
CISMs play a pivotal role in incident management. If a cybersecurity breach occurs, they coordinate incident response activities, assign team members to tasks, and ensure protocols are followed to minimize damage.
- Overseeing Compliance
They work closely with legal and IT teams to verify compliance with regulations like GDPR, HIPAA, or CMMC. Risks identified during the audit process may require changes to governance policies or staff training programs.
Afternoon Responsibilities
- Team Leadership
CISMs liaise with departmental heads, training employees on best practices and ensuring incident protocols are well-understood throughout the organization.
- Drafting Security Policies
Their afternoons can involve creating or refining cybersecurity guidelines, emphasizing areas like access control, vulnerability management, and business continuity.
Key Competencies for CISM Professionals:
- Governance of information security programs
- Incident management and response
- Balancing security with business functionality
The CISM professional exemplifies leadership, ensuring that IT operations are secure, compliant, and resilient in the face of threats.
Career Paths and Salary Expectations
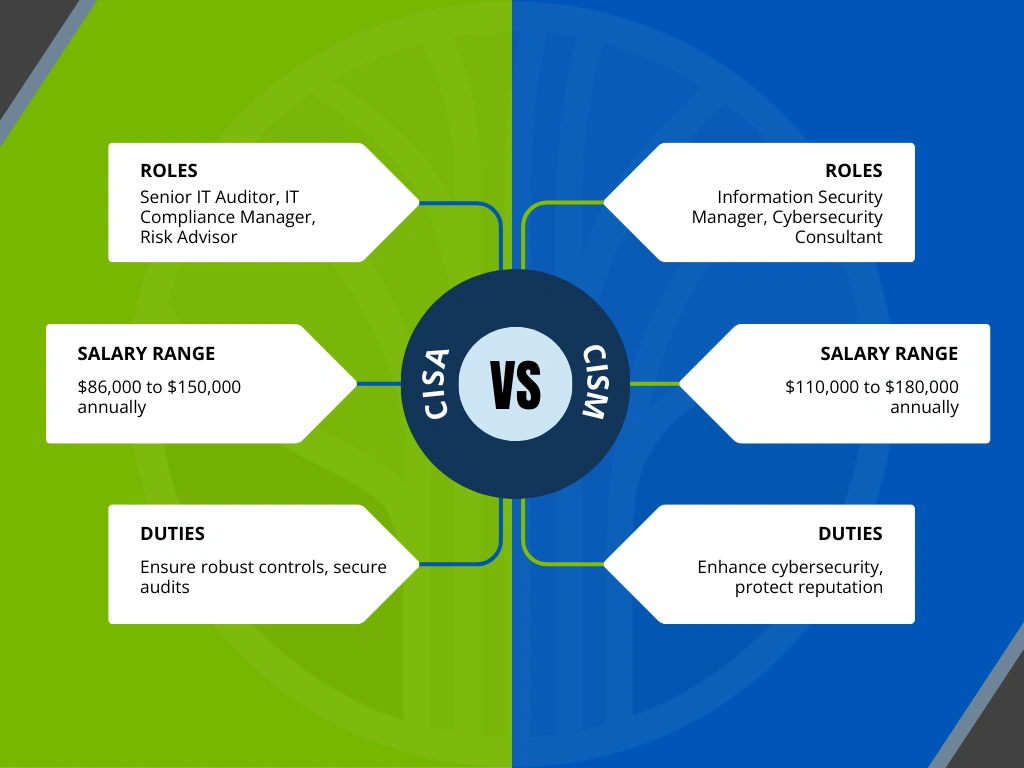
Clearly, both certifications offer lucrative opportunities.
Real-World Implications of CISA and CISM Certifications
Organizations benefit significantly from hiring or promoting CISA and CISM-certified professionals. CISAs ensure robust internal controls and secure audits, reducing costly errors. Conversely, CISMs drive strategic decisions that enhance overall cybersecurity resilience, protecting brand reputation and preventing regulatory fines.
By acquiring these credentials, you position yourself as a valuable asset in any tech-forward organization.
Final Thoughts and Next Steps
Whether you're drawn to the detailed audit workflows of a CISA or the strategic cybersecurity leadership of a CISM, both certifications can elevate your career as a trusted IT professional.
Take the leap today. Prepare, register, and earn your credential with ISACA to unlock new career milestones. Explore ISACA exam prep resources here and start building your professional legacy.
Further reading: Check out our recent article on this topic: How CISA and CISM Certifications Address Emerging Technologies like AI and Blockchain


